Updating e-mail security features on my server.
Sat 14 September 2019
I recently learned of a new security process called SMTP MTA Strict Transport Security, or MTA-STS for short. It’s not new, exactly, but it hasn’t been talked about a lot, either. Basically, it does what HTTP Strict Transport Security, HSTS, does for websites and informs the connecting client that not only is encryption available but it should be used, in this case for delivering mail to the SMTP server. Google officially rolled out support for this in April of this year and I am receiving reports that my rule is being used so that’s encouraging. This solves the opportunistic encryption vulnerability whereas a MITM attacker could downgrade an otherwise encrypted connection.
How MTA-STS actually works.
First, a mail client (usually a mail server) queries a DNS server to determine the domain’s MX record so it knows where to send the mail.
A mail client could also query the DNS server to determine if a MTA-STS record exists as well.
If the record exists, then the server connects to a predetermined URL (mta-sts.<domain>/.well-known/mta-sts.txt) and obtains the rule that has been established by the system owner.
This rule is cached by the system and doesn’t change unless the DNS record’s ID changes so, like HSTS, once the server connects the first time, it knows that it should always connect to that domain’s SMTP server(s) using encryption.
If there is a downgrade attack, or some other problem where encryption is not available, the connection fails and mail is not sent.
It should be noted that the DNS records should/must be secured with DNSSEC for this whole thing to work well.
But what about DANE?
Oh, lets not forget about DANE which is another great way of advertising encryption possibilities. DANE not only shows your encryption possibilities but also provides your public key so your clients can compare it when they connect. A bad actor trying to imitate you wouldn’t be able to unless they were able to steal your private key. And this isn’t HPKP where you can completely lock your domain off of the web for months because you lost control of your keys or did something incorrect.
So what feedback are you getting?
I’ve been running this for only a few days and, so far, I’ve received feedback from two providers: Google and Comcast. Google is using MTA-STS and has successfully read my rule and is enforcing encryption for all messages coming to my domain. Comcast is using DANE and is successfully sending messages to my domain not only encrypted but is verifying my certificate as well.
Others may also be using these technologies but not reporting using the RFC8460 SMTP TLS report.
By Sparks, Category: Information Security
Tags: SMTP / e-mail / encryption / opportunistic encryption /
Other articles
A response to 'Strong Encryption and Death'
Fri 20 January 2017
I recently read an article on the TriLUG blog mirror discussing access to data after the death of the owner. I've also given this a lot of thought as well and had previously come to the same conclusion as the original author of the article has:
"I created a file …
By Sparks, Category: Computers
Continue reading …Encryption you don't control is not a security feature
Wed 23 September 2015
Catching up on my blog reading, this morning, led me to an article discussing Apple's iMessage program and, specifically, the encryption it uses and how it's implemented. Go ahead and read the article; I'll wait.
The TL;DR of that article is this: encryption you don't control is not a …
By Sparks, Category: Information Security
Continue reading …Postfix Encryption
Thu 12 March 2015
I've been tinkering with the encryption options in Postfix for a while. Encryption between clients and their SMTP server and between SMTP servers is necessary to protect the to, from, and subject fields, along with the rest of the header, of an email. The body of the message is also …
By Sparks, Category: Information Security
Continue reading …Securing Secure Shell
Tue 06 January 2015
I was passed an interesting article, this morning, regarding hardening secure shell (SSH) against poor crypto that can be a victim of cracking by the NSA and other entities. The article is well written and discusses why the changes are necessary in light of recent Snowden file releases.
By Sparks, Category: Information Security
Continue reading …How to really screw up TLS
Fri 12 December 2014
I've noticed a few of my favorite websites failing with some odd error from Firefox.
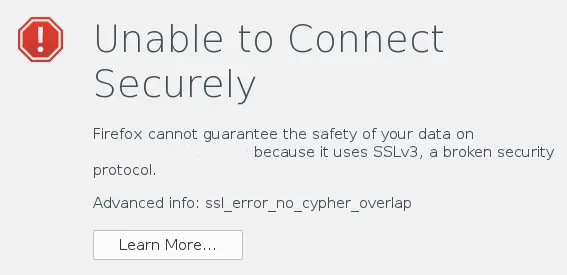 The Firefox error
message is a bit misleading. It actually has nothing to do with the
website supporting SSL 3.0 but the advanced info is spot on. The error
"ssl_error_no_cypher_overlap …
The Firefox error
message is a bit misleading. It actually has nothing to do with the
website supporting SSL 3.0 but the advanced info is spot on. The error
"ssl_error_no_cypher_overlap …
By Sparks, Category: Information Security
Continue reading …Automated configuration analysis for Mozilla's TLS guidelines
Thu 09 October 2014
My friend Hubert has been doing a lot of work to make better the world a little safer. Glad he's getting some recognition. Here's a great article on testing your server for proper SSL/TLS configurations.
By Sparks, Category: Radio
Continue reading …Generating a PGP key using GnuPG
Mon 16 June 2014
Generating a PGP using GnuPG (GPG) is quite simple. The following shows my recommendations for generating a PGP key today.
$ gpg --gen-key gpg (GnuPG) 1.4.16; Copyright (C) 2013 Free Software Foundation, Inc. This is free software: you are free to change and redistribute it. There is NO WARRANTY …
By Sparks, Category: Information Security
Continue reading …SSL/TLS Trends
Tue 20 May 2014
My friend Hubert has started compiling statistics of Alexa's top 1 million websites. Specifically, he's looking at their SSL/TLS settings and attempting to show trends in the world that is port 443. He recently released his May numbers showing a slow but mostly improving security environment. I'm hoping he'll …
By Sparks, Category: Information Security
Continue reading …STARTTLS for SMTP
Thu 15 May 2014
Okay, I don't really mean to advocate this as a privacy solution because it is and it isn't. If you truly want privacy of your email you mustuse end-to-end encryption like PGP/GnuPG or S/MIME. That said, I think it's good to encrypt things, even ciphertext, over the …
By Sparks, Category: Information Security
Continue reading …256 Bits of Security
Thu 17 April 2014
This is an incomplete discussion of SSL/TLS authentication and encryption. This post only goes into RSA and does not discuss DHE, PFS, elliptical, or other mechanisms.
In a previous post I created an 15,360-bit RSA key and timed how long it took to create the key. Some may …
By Sparks, Category: Information Security
Continue reading …Time to generate a 15,360-bit RSA key
Tue 15 April 2014
<magic happens>
By Sparks, Category: Information Security
Continue reading …Kicking RC4 out the door
Wed 13 November 2013
I've been arguing with my web hosting company about their use of RC4. Like many enterprise networks they aren't consistent across all their servers with respect to available ciphers and such. It appears that all customer servers support TLS_RSA_WITH_CAMELLIA_256_CBC_SHA and TLS_RSA_WITH_CAMELLIA …
By Sparks, Category: Information Security
Continue reading …How secure are those SSL and SSH keys anyway?
Wed 30 October 2013
Thought I'd pass along this research study, The keys to the kingdom, as I found it to be quite interesting (especially when you scan the entire Internet for your data). If you don't understand the math explanation at the beginning just continue reading as you don't need to have a …
By Sparks, Category: Information Security
Continue reading …Why Android SSL was downgraded from AES256-SHA to RC4-MD5 in late 2010
Mon 14 October 2013
Just ran across this article discussing how horrible the cipher preference list is in Android. That's a lot of bad crypto on the streets right now.
Why Android SSL was downgraded from AES256-SHA to RC4-MD5 in late 2010
By Sparks, Category: Information Security
Continue reading …Trusting Trusted CAs
Wed 09 October 2013
Like it or not, the basis of trust for much of the Internet is based on Certificate Authorities (CA). Companies like Verisign, GoDaddy, and GeoTrust are in the trust business. They will sell you cryptographic proof of your Internet assets (namely your domain name) that others can use to verify …
By Sparks, Category: Information Security
Continue reading …Tor and HTTPS
Wed 17 July 2013
An excellent description of how Tor and HTTPS can help protect your online privacy and secure your web communications.
By Sparks, Category: Information Security
Continue reading …Secure GnuPG configuration
Tue 09 July 2013
Someone recently asked what my GPG.conf file looks like since he hadn't updated his in... years. Okay, let's take a look and I'll try to explain what each setting is and why I feel it is important. I'm not guaranteeing this as being complete and I welcome input from …
By Sparks, Category: Information Security
Continue reading …Inadvertant data leakage from GnuPG
Mon 01 July 2013
I was recently introduced to a privacy issue when refreshing your OpenPGP keys using GnuPG. When refreshing your public key ring using a public key server GnuPG will generally use the OpenPGP HTTP Key Protocol (HKP) to synchronize keys. The problem is that when you do refresh your keys using …
By Sparks, Category: Information Security
Continue reading …Encrypting SMS messages and phone calls on Android
Thu 21 March 2013
Much of our daily lives are contained within our smartphones and computers. Email, text messages, and phone calls all contain bits and pieces of information that, in the wrong hands, could harm our privacy. Unfortunately many people either don't understand how vulnerable their data is when sent across the Internet …
By Sparks, Category: Information Security
Continue reading …GeekNote: PGP/GnuPG Key Statistics Tools
Sun 02 October 2011
PGP Pathfinder and Key Statistics
https://listman.redhat.com/archives/rhl-devel-list/2008-January/msg00710.html
By Sparks, Category: Information Security
Continue reading …Proposed encryption "backdoor" for the US Government and how it will fail.
Tue 28 September 2010
If you haven't heard, the President is drafting legislation that may require hardware and software developers to install backdoors in their encryption solutions and give the keys to these backdoors to the US Government. In my opinion, this is an increadibly bad idea.
- This has already been tried and failed …
By Sparks, Category: Information Security
Continue reading …Protecting your email from disclosure
Mon 07 December 2009
Climate talk, Alaska government business, and Dave Briggs. What do these three things have in common? Each of these subjects had more light shown on them by someone cracking email messages and releasing those messages to the public over the Internet. Of course there are many more of these events …
By Sparks, Category: Information Security
Continue reading …Securing Instant Messaging
Tue 26 May 2009
More and more sensitive communications are occurring over unsecure instant messaging (IM) systems. These messages go through a third-party and can be read anywhere along the way. An easy, open-source solution does exist to help protect these communications, however.
First you need the IM client called Pidgin. This client works …