How to really screw up TLS
Fri 12 December 2014
I've noticed a few of my favorite websites failing with some odd error from Firefox.
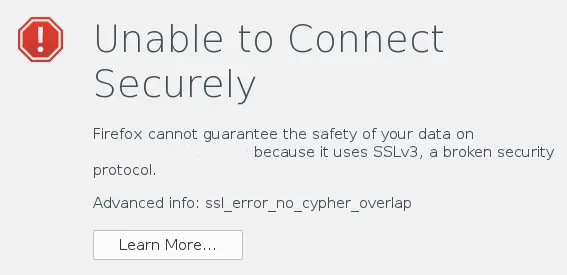 The Firefox error
message is a bit misleading. It actually has nothing to do with the
website supporting SSL 3.0 but the advanced info is spot on. The error
"ssl_error_no_cypher_overlap" means that the client didn't offer any
ciphers that the server also supports. Generally when I see this I
assume that the server has been setup poorly and only supports unsafe
ciphers. In this case the website only supports the RC4 cipher. I
wondered why I was starting to see a reversal of removing RC4 from so
many websites recently (especially since RC4 is very
weak
and is on the way
out).
Apparently these websites all use the F5 load balancer that had a bad
implementation of the TLS 1.0 standard causing a POODLE-like
vulnerability.
The Firefox error
message is a bit misleading. It actually has nothing to do with the
website supporting SSL 3.0 but the advanced info is spot on. The error
"ssl_error_no_cypher_overlap" means that the client didn't offer any
ciphers that the server also supports. Generally when I see this I
assume that the server has been setup poorly and only supports unsafe
ciphers. In this case the website only supports the RC4 cipher. I
wondered why I was starting to see a reversal of removing RC4 from so
many websites recently (especially since RC4 is very
weak
and is on the way
out).
Apparently these websites all use the F5 load balancer that had a bad
implementation of the TLS 1.0 standard causing a POODLE-like
vulnerability.
Stepping back for a moment, back in October the POODLE vulnerability hit the streets and a mass exodus from SSL 3.0 happened around the world. I was happy to see so many people running away from the broken cryptographic protocol and very happy to see the big push to implementing the latest version of TLS, TLS 1.2. So with SSL 3.0 out of the way and the POODLE vulnerability being squelched why are we seeing problems in TLS 1.0 now?
Well, simply put, F5 load balancers don't implement TLS 1.0 correctly. The problem with SSL 3.0 is that the padding format isn't checked. Apparently in the F5 devices it's still a problem in TLS 1.0. And while the company did offer up patches to fix the issue, some really bad advice has been circulating the Internetz telling people to only support RC4, again. Sigh.
When RC4 finally dies a fiery death I'll likely throw a party. I'm sure I won't be the only one...
By Sparks, Category: Information Security
Tags: RC4 / SSL / TLS / Confidentiality / Encryption /
Other articles
Kicking RC4 out the door
Wed 13 November 2013
I've been arguing with my web hosting company about their use of RC4. Like many enterprise networks they aren't consistent across all their servers with respect to available ciphers and such. It appears that all customer servers support TLS_RSA_WITH_CAMELLIA_256_CBC_SHA and TLS_RSA_WITH_CAMELLIA …
By Sparks, Category: Information Security
Continue reading …Why Android SSL was downgraded from AES256-SHA to RC4-MD5 in late 2010
Mon 14 October 2013
Just ran across this article discussing how horrible the cipher preference list is in Android. That's a lot of bad crypto on the streets right now.
Why Android SSL was downgraded from AES256-SHA to RC4-MD5 in late 2010