
OCSP Vulnerability in Nextcloud client
Thu 09 June 2022

Online Certificate Status Protocol (OCSP) is a method for determining the revocation status of a X.509 digital certificate used to authenticate a website, service, or user. Basically, a web browser can, before deciding to use a particular certificate for an encrypted session[1], verify that the certificate is still valid instead of just relying on an expiration date. While many (most?) certificates are good until expiration, one never knows if a certificate gets replaced due to compromise or because the certificate was upgraded. This is why OCSP exists; to provide a mechanism to notify the end-device that the certificate is no longer in use and that it shouldn’t be trusted.
Back in January of 2022, I discovered that Nextcloud client does not check the status of certificates. I was in the process of swapping out some certificates and my computer readily accepted a revoked certificate as trusted. I opened a bug against the product to let the developers know of the issue; it should be a relatively easy fix. Today, five months later, I was told that:
After some discussion and getting a broader picture of the situation and consequences, it was decided that we will not fix this.
So, with that out of the way, I now disclose this to you fine people to do what you will with the information. Hopefully you will not be adversely affected by this bug and I’m not sure exactly how difficult it would be to fix it. If they are simply calling openssl then it’s likely just adding the proper switch. I, unfortunately, have not gotten that far into the issue just yet.
By Sparks, Category: Information Security
Tags: Nextcloud / CWE-200 / OCSP /
Other articles
Multi Factor Authentication Tokens
Tue 24 May 2022
There are many types of multi factor authentication (MFA) tokens available. Some are virtual, some are software (apps), and some are hardware. Each has their benefits and their disadvantages. This paper discusses some of the concerns with each type of authentication token type and what is recommended for secure networks …
By Sparks, Category: Information Security
Continue reading …Signal routing
Mon 19 October 2020
Made a Signal call to a friend today. He was curious and pulled up Wireshark to see how the call was being routed. It appears that our call was going point-to-point, over IPv6 (no NAT), directly between devices.
So, as the Internet was designed…
By Sparks, Category: Information Security
Continue reading …DMARC Works
Tue 01 September 2020
Earlier today I received a few notifications of bounced mail from Google. This was odd seeing as how I hadn’t sent any mail to Google in a while. Upon further inspection, the messages originated from an application running on one of my servers. These were password reset messages destined …
By Sparks, Category: Information Security
Continue reading …E-mail Security
Wed 01 July 2020
Way back when, e-mail was from server-to-server, and really client-to-server as well, without much thought to security. Messages were transmitted in plain text (no encryption) and the only people reading your mail (literally) were the system administrators who ran the email server. Of course, those system administrators knew what was …
By Sparks, Category: Information Security
Continue reading …Updating e-mail security features on my server.
Sat 14 September 2019
I recently learned of a new security process called SMTP MTA Strict Transport Security, or MTA-STS for short. It’s not new, exactly, but it hasn’t been talked about a lot, either. Basically, it does what HTTP Strict Transport Security, HSTS, does for websites and informs the connecting client …
By Sparks, Category: Information Security
Continue reading …Security of Shredding Services
Mon 04 February 2019
When I started dealing with serious information security we created a lot of paper. This wasn’t regular information printed on paper but very sensitive information that could be very damaging if it ever found its way out of the building. If this paper was ever deemed to be trash …
By Sparks, Category: Information Security
Continue reading …A review of ProtonMail
Wed 02 May 2018
Update (2018-07-25)
Shortly after publishing this original post, many of my concerns were addressed. ProtonMail now supports sending mail that is signed and/or encrypted using OpenPGP. This is a huge benefit to the secure-email community. It is also possible to use your own key which allows me to use …
By Eric H. Christensen, Category: Information Security
Continue reading …Ditch All Those Other Messaging Apps: Here's Why You Should Use Signal
Wed 21 February 2018
Completely agree!
https://www.wired.com/story/ditch-all-those-other-messaging-apps-heres-why-you-should-use-signal/
By Sparks, Category: Information Security
Continue reading …Content Security Policy and WordPress
Sun 14 January 2018
For your protection, I've been working on securing this website with all the proper security HTTP headers. Of course, by running WordPress as the backend, I'm making it easy to manage all the data but making it difficult to manage all the pieces and parts of the system's backend. The …
By Sparks, Category: Information Security
Continue reading …Securing email to Gmail
Tue 22 December 2015
I've been working on securing my postfix configuration to enforce certificate validation and encryption on some known, higher-volume, or more sensitive connections between SMTP servers (port 25).
On many of the connections I've setup for secure transport there have been no problems (assuming proper TLS certificates are used). Unfortunately Gmail …
By Sparks, Category: Information Security
Continue reading …RFC: Using video conferencing for GPG key signing events
Thu 24 September 2015
A thought that I haven't had a chance to fully consider (so I'm asking the Internet to do that for me)...
I have a geographically-diverse team that uses GPG to provide integrity of their messages. Usually, a team like this would all huddle together and do a formal key-signing event …
By Sparks, Category: Information Security
Continue reading …Encryption you don't control is not a security feature
Wed 23 September 2015
Catching up on my blog reading, this morning, led me to an article discussing Apple's iMessage program and, specifically, the encryption it uses and how it's implemented. Go ahead and read the article; I'll wait.
The TL;DR of that article is this: encryption you don't control is not a …
By Sparks, Category: Information Security
Continue reading …Postfix Encryption
Thu 12 March 2015
I've been tinkering with the encryption options in Postfix for a while. Encryption between clients and their SMTP server and between SMTP servers is necessary to protect the to, from, and subject fields, along with the rest of the header, of an email. The body of the message is also …
By Sparks, Category: Information Security
Continue reading …Securing Secure Shell
Tue 06 January 2015
I was passed an interesting article, this morning, regarding hardening secure shell (SSH) against poor crypto that can be a victim of cracking by the NSA and other entities. The article is well written and discusses why the changes are necessary in light of recent Snowden file releases.
By Sparks, Category: Information Security
Continue reading …How to really screw up TLS
Fri 12 December 2014
I've noticed a few of my favorite websites failing with some odd error from Firefox.
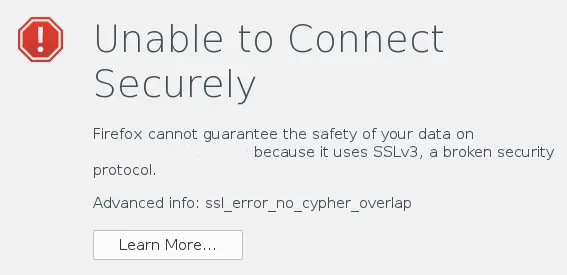 The Firefox error
message is a bit misleading. It actually has nothing to do with the
website supporting SSL 3.0 but the advanced info is spot on. The error
"ssl_error_no_cypher_overlap …
The Firefox error
message is a bit misleading. It actually has nothing to do with the
website supporting SSL 3.0 but the advanced info is spot on. The error
"ssl_error_no_cypher_overlap …
By Sparks, Category: Information Security
Continue reading …Ability to remove TLS 1.0 from httpd in CentOS 6
Thu 30 October 2014
Due to a bug in mod_ssl, the ability to remove TLS 1.0 (and only support TLS 1.1 and/or TLS 1.2) has not been available. The fix has now made it to CentOS 6 and you can now fine-tune your cryptographic protocols with ease.
Before the …
By Sparks, Category: Information Security
Continue reading …Okay, this is a neat attack...
Fri 22 August 2014
This morning I received an email from my "administrator" saying that I needed to validate my email address within the next 48 hours or my email account would be suspended. Seeing as how I'm my own email administrator, I couldn't remember sending out such a message, I decided that this …
By Sparks, Category: Information Security
Continue reading …Signing PGP keys
Sat 21 June 2014
If you've recently completed a key signing party or have otherwise met up with other people and have exchanged key fingerprints and verified IDs, it's now time to sign the keys you trust. There are several different ways of completing this task and I'll discuss two of them now.
caff …
By Sparks, Category: Information Security
Continue reading …PGP Keysigning Event and CACert Assertion at SELF2014
Mon 16 June 2014
SouthEast LinuxFest is happening this upcoming weekend. I offered to host a PGP (I'll substitute PGP for GPG, GnuPG, and other iterations) keysigning and CACert Assertion event and have been scheduled for 6:30 PM in the Red Hat Ballroom. Since there is a little bit of planning needed on …
By Sparks, Category: Information Security
Continue reading …Generating a PGP key using GnuPG
Mon 16 June 2014
Generating a PGP using GnuPG (GPG) is quite simple. The following shows my recommendations for generating a PGP key today.
$ gpg --gen-key gpg (GnuPG) 1.4.16; Copyright (C) 2013 Free Software Foundation, Inc. This is free software: you are free to change and redistribute it. There is NO WARRANTY …
By Sparks, Category: Information Security
Continue reading …Secure E-mail
Thu 29 May 2014
E-mail is inherently insecure. Just as sending a post card, any message sent by e-mail can be read by any number of people, including those monitoring the network path, the servers that process the message along its route, or anyone with access to the distant computer. Basically you should consider …
By Sparks, Category: Information Security
Continue reading …SSL/TLS Trends
Tue 20 May 2014
My friend Hubert has started compiling statistics of Alexa's top 1 million websites. Specifically, he's looking at their SSL/TLS settings and attempting to show trends in the world that is port 443. He recently released his May numbers showing a slow but mostly improving security environment. I'm hoping he'll …
By Sparks, Category: Information Security
Continue reading …STARTTLS for SMTP
Thu 15 May 2014
Okay, I don't really mean to advocate this as a privacy solution because it is and it isn't. If you truly want privacy of your email you mustuse end-to-end encryption like PGP/GnuPG or S/MIME. That said, I think it's good to encrypt things, even ciphertext, over the …
By Sparks, Category: Information Security
Continue reading …256 Bits of Security
Thu 17 April 2014
This is an incomplete discussion of SSL/TLS authentication and encryption. This post only goes into RSA and does not discuss DHE, PFS, elliptical, or other mechanisms.
In a previous post I created an 15,360-bit RSA key and timed how long it took to create the key. Some may …
By Sparks, Category: Information Security
Continue reading …Time to generate a 15,360-bit RSA key
Tue 15 April 2014
<magic happens>
By Sparks, Category: Information Security
Continue reading …Kicking RC4 out the door
Wed 13 November 2013
I've been arguing with my web hosting company about their use of RC4. Like many enterprise networks they aren't consistent across all their servers with respect to available ciphers and such. It appears that all customer servers support TLS_RSA_WITH_CAMELLIA_256_CBC_SHA and TLS_RSA_WITH_CAMELLIA …
By Sparks, Category: Information Security
Continue reading …How secure are those SSL and SSH keys anyway?
Wed 30 October 2013
Thought I'd pass along this research study, The keys to the kingdom, as I found it to be quite interesting (especially when you scan the entire Internet for your data). If you don't understand the math explanation at the beginning just continue reading as you don't need to have a …
By Sparks, Category: Information Security
Continue reading …Why Android SSL was downgraded from AES256-SHA to RC4-MD5 in late 2010
Mon 14 October 2013
Just ran across this article discussing how horrible the cipher preference list is in Android. That's a lot of bad crypto on the streets right now.
Why Android SSL was downgraded from AES256-SHA to RC4-MD5 in late 2010
By Sparks, Category: Information Security
Continue reading …Trusting Trusted CAs
Wed 09 October 2013
Like it or not, the basis of trust for much of the Internet is based on Certificate Authorities (CA). Companies like Verisign, GoDaddy, and GeoTrust are in the trust business. They will sell you cryptographic proof of your Internet assets (namely your domain name) that others can use to verify …
By Sparks, Category: Information Security
Continue reading …SFGate: If You Send To Gmail, You Have 'No Legitimate Expectation Of Privacy'
Thu 15 August 2013
SFGate: If You Send To Gmail, You Have 'No Legitimate Expectation Of Privacy'
Not that this is really news but if you hand your message to a third-party for delivery you have no expectation of privacy. Agree with it or not that's the way it is inside the United States …
By Sparks, Category: Information Security
Continue reading …Tor and HTTPS
Wed 17 July 2013
An excellent description of how Tor and HTTPS can help protect your online privacy and secure your web communications.
By Sparks, Category: Information Security
Continue reading …Lawmakers of both parties voice doubts about NSA surveillance programs
Wed 17 July 2013
Lawmakers of both parties voice doubts about NSA surveillance programs
I'm happy to read the Washington Post story discussing the House committee's hearing on the NSA's domestic spying programs. It's encouraging that both parties aren't happy with the programs and that "...there are not enough votes in the House now …
By Sparks, Category: Information Security
Continue reading …Privacy articles to read
Tue 09 July 2013
Why Privacy Matters Even if You Have 'Nothing to Hide' by The Chronicle Review
Using Metadata to Find Paul Revere by Kieran Healy
We Should All Have Something To Hide by Moxie Marlinspike
By Sparks, Category: Information Security
Continue reading …Secure GnuPG configuration
Tue 09 July 2013
Someone recently asked what my GPG.conf file looks like since he hadn't updated his in... years. Okay, let's take a look and I'll try to explain what each setting is and why I feel it is important. I'm not guaranteeing this as being complete and I welcome input from …
By Sparks, Category: Information Security
Continue reading …Inadvertant data leakage from GnuPG
Mon 01 July 2013
I was recently introduced to a privacy issue when refreshing your OpenPGP keys using GnuPG. When refreshing your public key ring using a public key server GnuPG will generally use the OpenPGP HTTP Key Protocol (HKP) to synchronize keys. The problem is that when you do refresh your keys using …
By Sparks, Category: Information Security
Continue reading …The Guardian: I'd pay more for tech products with greater privacy from surveillance
Wed 26 June 2013
The Guardian: I'd pay more for tech products with greater privacy from surveillance
I thought this was a fantastic article. It skims over the fact that if you aren't paying for a service then you are probably the product being sold. Google, Facebook, and many other companies make billions of …
By Sparks, Category: Information Security
Continue reading …Encrypting SMS messages and phone calls on Android
Thu 21 March 2013
Much of our daily lives are contained within our smartphones and computers. Email, text messages, and phone calls all contain bits and pieces of information that, in the wrong hands, could harm our privacy. Unfortunately many people either don't understand how vulnerable their data is when sent across the Internet …
By Sparks, Category: Information Security
Continue reading …Port scanning /0 using insecure embedded devices
Wed 20 March 2013
Someone sent me a link to the Port scanning /0 using insecure embedded devices article that was recently published. Describing the Carna Botnet, this project aimed to prove (or disprove) the hypothesis that there were one hundred thousand open systems on the Internet in which to make a botnet. I …
By Sparks, Category: Information Security
Continue reading …Privacy Upgrade: Encrypted Internet browsing
Thu 14 March 2013
Many websites have both the traditional, unencrypted HTTP and the SSL or TLS-encrypted HTTPS addresses available to access their content. Wikipedia is one good example of this functionality. You can easily view Wikipedia using traditional HTTP protocol but if you wanted or needed a little more privacy the HTTPS …
By Sparks, Category: Information Security
Continue reading …How PGP actually works...
Mon 04 March 2013
CC BY-NC xkcd
By Sparks, Category: Information Security
Continue reading …The dangers of mandatory software on smartphones
Mon 04 March 2013
I awoke this morning to find an email from Evernote, the company that has the product of the same name for note taking, saying that they had been hacked and that I should change my password. T-Mobile installs this software, along with many other pieces of software, on my smartphone …
By Sparks, Category: Information Security
Continue reading …Removing dependencies when using yum
Fri 01 March 2013
 A forthcoming article on the Red Hat
Security Blog got me to ask the
question: is it possible to have yum remove dependencies when
uninstalling packages? The answer is a somewhat surprising "yes"! The
functionality is turned off by default for a good reason but that's no
reason why everyone …
A forthcoming article on the Red Hat
Security Blog got me to ask the
question: is it possible to have yum remove dependencies when
uninstalling packages? The answer is a somewhat surprising "yes"! The
functionality is turned off by default for a good reason but that's no
reason why everyone …
By Sparks, Category: Information Security
Continue reading …Hashing Algorithm: Is your GPG configuration secure?
Thu 21 February 2013
If your email messages are being signed using SHA-1 you may not be getting the security you think you are. Attacks on the hashing algorithm have caused much pain to those that use it. Luckily SHA-2 is available and hopefully we'll start seeing SHA-3 out in the world soon.
You've …
By Sparks, Category: Information Security
Continue reading …US-CERT: Java vulnerability
Fri 11 January 2013
A bad (as in it's a 10) Java vulnerability has been discovered. Affecting Java 7 Update 10 and prior versions, this vulnerability can allow an untrusted Java applet to escalate its privileges without requiring code signing.
Currently, the only defense to this vulnerability is to disable Java in your browser …
By Sparks, Category: Information Security
Continue reading …Password strength, more characters are better than complexity
Thu 26 July 2012
In a recent PBS Newshour article discussing the recent Yahoo! password list theft, a reference to a chart showing howshort passwords can still be secure was added to the story. The data and conclusions included in that chart were disturbing to me, to say the least. While complexity does …
By Sparks, Category: Information Security
Continue reading …New year, updated keys.
Tue 03 January 2012
 I run a SKS key server and watch my daily numbers to see
how many keys get updated, etc. Being a numbers guy I wondered how many
people, like me, update their GPG keys, I specifically update the
expiration date and generate new encryption keys annually, at the
beginning of …
I run a SKS key server and watch my daily numbers to see
how many keys get updated, etc. Being a numbers guy I wondered how many
people, like me, update their GPG keys, I specifically update the
expiration date and generate new encryption keys annually, at the
beginning of …
By Sparks, Category: Information Security
Continue reading …End user security for web browsing
Sat 31 December 2011
Someone asked me, earlier this week, how to setup a "very secure Fedora 16..." system for a user that mostly surfs the web and uses email. Instead of responding directly to that user I'm writing this in order to get others to comment and provide additional information that I may …
By Sparks, Category: Information Security
Continue reading …GeekNote: PGP/GnuPG Key Statistics Tools
Sun 02 October 2011
PGP Pathfinder and Key Statistics
https://listman.redhat.com/archives/rhl-devel-list/2008-January/msg00710.html
By Sparks, Category: Information Security
Continue reading …Complex, secure passwords made easy
Thu 29 September 2011
I attended a talk by Aaron Toponce at Ohio Linux Fest on password security. Everyone knows you shouldn't use a simple password that is easily guessable and that you shouldn't use the same password for every account but how do you make unique, complex passwords and only use it once …
By Sparks, Category: Information Security
Continue reading …Does Google's multi-factor authentication make your security weaker?
Mon 20 June 2011
A few months back Google introduced "2-step verification" for all Google accounts. This amounted to multi-factor authentication (something you know (password) and something you have (token)) for all web-based Google applications. Cool, right? They created an app for the Android, I-Phone, and Blackberry devices that acted like a token and …
By Sparks, Category: Information Security
Continue reading …FOSS solutions could help when communication failures occur.
Sat 29 January 2011
Not to get into the political battle that is occurring in Egypt but I wonder how the organization of both news gathering agencies and organizers would have fared had they been using StatusNet software (the software that supports identi.ca) on a local computer inside the country instead of utilizing …
By Sparks, Category: Information Security
Continue reading …I'm going to need a few more Yubikeys...
Mon 18 October 2010
Last week I received my Yubikey and promptly figured out how to use it with my Drupal installation using the Yubico authentication server. Since then life got in the way and I haven't had a chance to work on my other projects that I want to get working. I did …
By Sparks, Category: Information Security
Continue reading …Proposed encryption "backdoor" for the US Government and how it will fail.
Tue 28 September 2010
If you haven't heard, the President is drafting legislation that may require hardware and software developers to install backdoors in their encryption solutions and give the keys to these backdoors to the US Government. In my opinion, this is an increadibly bad idea.
- This has already been tried and failed …
By Sparks, Category: Information Security
Continue reading …HTTPS-Everywhere
Mon 21 June 2010
The other day I found myself reading about a new Firefox plugin that will automatically select HTTPS for various websites (and you can make your own rules, too). The plugin, created by the EFF, is named HTTPS Everywhere.
Basically it knows that there are several popular websites out there that …
By Sparks, Category: Information Security
Continue reading …Privacy risk in your email client?
Tue 02 February 2010
By Sparks, Category: Information Security
Continue reading …Protecting your email from disclosure
Mon 07 December 2009
Climate talk, Alaska government business, and Dave Briggs. What do these three things have in common? Each of these subjects had more light shown on them by someone cracking email messages and releasing those messages to the public over the Internet. Of course there are many more of these events …
By Sparks, Category: Information Security
Continue reading …Expiring OpenPGP keys...
Mon 19 October 2009
A discussion was had on one of the Fedora IRC channels months ago about the "proper" way to handle expiring GPG keys without breaking the web of trust. It was my opinion that by generating new keys every so often (yearly?) that it would increase the security of the overall …
By Sparks, Category: Information Security
Continue reading …Securing Instant Messaging
Tue 26 May 2009
More and more sensitive communications are occurring over unsecure instant messaging (IM) systems. These messages go through a third-party and can be read anywhere along the way. An easy, open-source solution does exist to help protect these communications, however.
First you need the IM client called Pidgin. This client works …
By Sparks, Category: Information Security
Continue reading …Plaintext Recovery Attack Against OpenSSH
Tue 18 November 2008
https://isc.sans.edu/diary/Plaintext+Recovery+Attack+Against+OpenSSH/5366
SANS Internet Storm Center is reporting an attack against OpenSSH. Please go to the link above for more information as they are posting updates there.
By Sparks, Category: Information Security
Continue reading …Open Source down falls when dealing with the US Government
Fri 15 August 2008
I don't hide the fact that I am a contractor to a few US Government organizations and deal specifically with security issues. As such, I'm asked if I'm seeing any open source or Linux items in my daily work. Unfortunately the answer is always "not as much as I'd like …
By Sparks, Category: Information Security
Continue reading …SANS ISC goes to YELLOW: SSH vulnerability
Thu 15 May 2008
SANS Internet Storm Center has raised the Internet Threat Level to YELLOW in response to a report of a SSH vulnerability on all Debian-based systems that generated SSH keys between September 2003 and 13 May 2008.
By Sparks, Category: Information Security
Continue reading …Internet Backbone Outage Reported in the Middle-East
Thu 31 January 2008
SANS Internet Storm Center is reporting that possibly several under-sea cables have been cut near the coast of Egypt. Several countries in that area have reported slow connections or complete packet loss. India is experiencing a 50% packet loss at times due to all their traffic having to flow out …
By Sparks, Category: Information Security
Continue reading …Problems at Radio Station W4OTN
Thu 22 November 2007
I've been having problems with my radio station lately and it has really started to bother me. I've used two antennas and haven't been satisfied with either one of them. Before I was using a 40-80-160 dipole but the 80m portion was too long and didn't want to work right …
